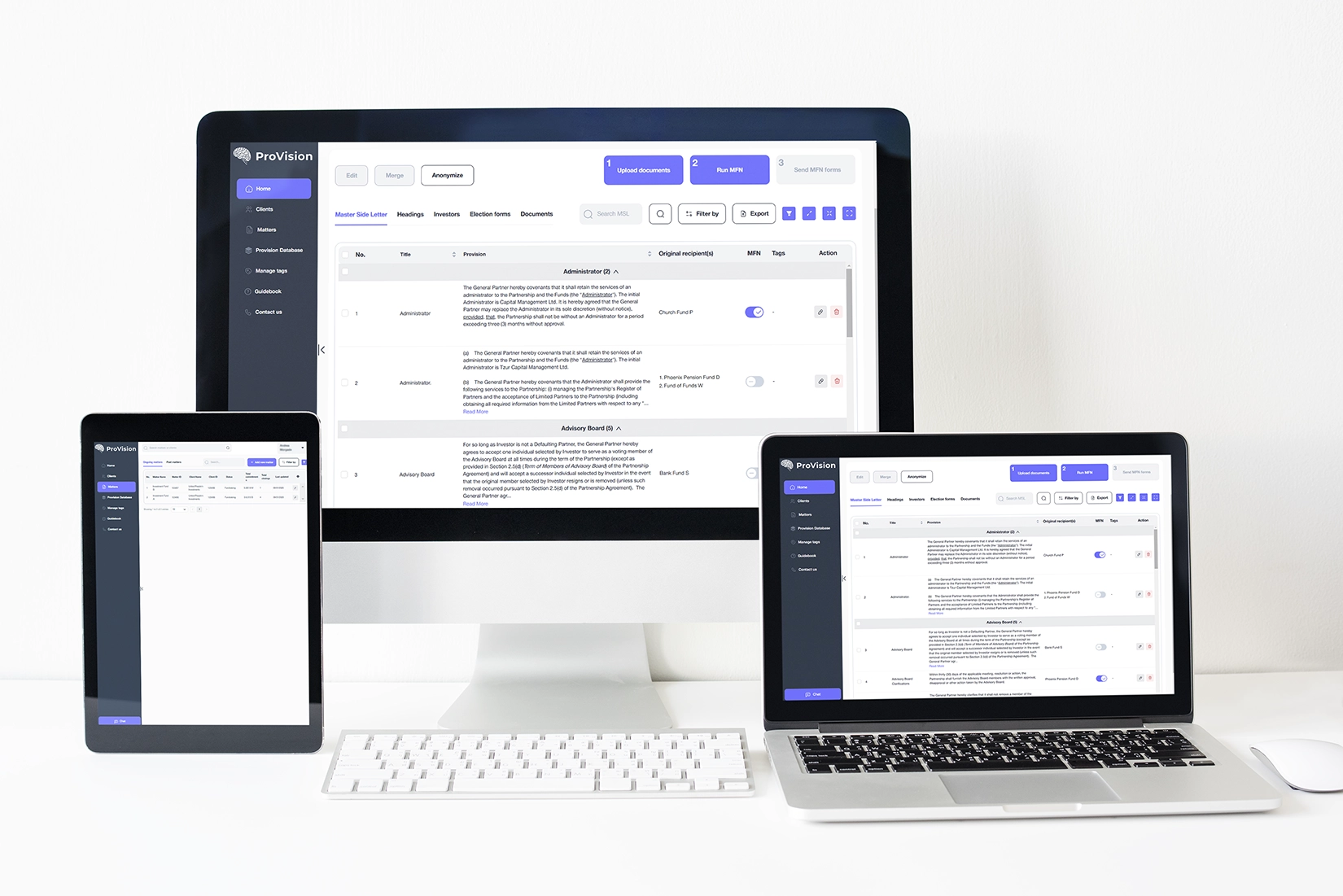
Data Security is at the Core of Our Platform
Encryption and Protection
- Data is encrypted both in transit and at rest using AWS Key Management Service.
Identity and Access Management
- We use IAM policies and role-based access controls to secure user access.
Network Security
- We deploy a proprietary mix of Virtual Private Cloud (VPC), Security Groups, and firewalls to protect the platform.
Need more information or have specific questions? Contact us to learn how we can assist you further.